this post was submitted on 06 Oct 2024
735 points (90.8% liked)
Technology
75373 readers
4744 users here now
This is a most excellent place for technology news and articles.
Our Rules
- Follow the lemmy.world rules.
- Only tech related news or articles.
- Be excellent to each other!
- Mod approved content bots can post up to 10 articles per day.
- Threads asking for personal tech support may be deleted.
- Politics threads may be removed.
- No memes allowed as posts, OK to post as comments.
- Only approved bots from the list below, this includes using AI responses and summaries. To ask if your bot can be added please contact a mod.
- Check for duplicates before posting, duplicates may be removed
- Accounts 7 days and younger will have their posts automatically removed.
Approved Bots
founded 2 years ago
MODERATORS
you are viewing a single comment's thread
view the rest of the comments
view the rest of the comments
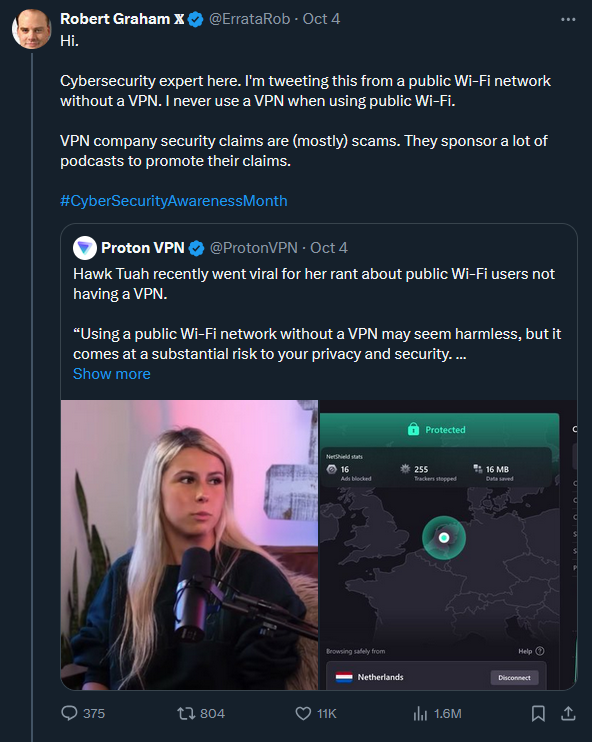
They need to advertise a legitimate use for their service.
If they don't have a threat from public wifi or other security concerns to remedy, then the only purpose for their service is to bypass region limits and block infringement notices. They would be considered complicit in such infringement.
That their service also hinders efforts to stop pirates needs to be an "unintended" and "unavoidable" side effect.
I use Proton when I'm on my university's campus because they switched to using EDUroam for the campus wifi. I used to be a Sys Admin at a different university a while back, and from what I know, EDUroam allows the IT department to monitor basically all of the traffic over the network. I don't know exactly how deep that stuff goes, but if I was doing anything personal or sensitive like banking or whatever, I'd flip on the VPN on my personal computer. I also don't have any personal accounts logged in on the school issued laptop because they have it loaded with institutional spyware. Once I graduate, I'll blank the drive and reinstall the OS to have a decent Lenovo laptop on hand as a spare.
Edit to add: I use Proton because it was the least shady service that I could get for a reasonable price as a student. It is also helpful for finding textbooks. :)
They can't decrypt HTTPS unless you installed a certificate controlled by them. The only thing they can know is which domains you visited, but not what you did on it.
They require the certificate to be installed to have access to the network.
There are plenty of legitimate uses for their services, they just aren't things that the vast majority of people actually need. For example:
There are also some sketchier needs, such as:
I think VPNs are trying to appeal to more than just the above needs, they're trying to create needs to grow their marketshare. That isn't something a reputable VPN should do, or at least that's something that would make me hesitate to use a given VPN.
If you want to give an anonymous video to the press or the police. If you don't hide your ip then it isn't anonymous and they'll come question you.
That's not a legitimate use; it's an illegal use just like piracy is.
ECH will finally fix this. https://blog.cloudflare.com/encrypted-client-hello/
SNI is still better than what we used to have. Before SNI, every site that used TLS or SSL had to have a dedicated IP address.
My understanding of the law (and yes, I read it) is that it's not illegal. The law in my state is for service providers to authenticate the ID of any state resident, it's not a requirement on the resident themselves. The service provider isn't aware what state I'm a resident of, and state law doesn't apply outside the state, so I don't know what law would be violated here.
I absolutely agree, and I actually use SNI to route packets for my homelab. Without SNI, I would have to route after handling certificates, which would be annoying because I want TLS to work within my home network, and I mess w/ DNS records to point to my local IPs when inside my network. I could have everything routed through a central hub (so one dedicated machine that handles all TLS), but that's a single point of failure, and I'm not too happy about that. Or I guess I'd have multiple IPs, and route based on which IP is being hit.
I'll have to check out ECH. Hopefully I can eat my cake and have it too.
The only thing you need to say is "my ISP uses CGNAT" you can't host anything or run games for your friends without a way to punch through the CGNAT layer. I mean you could use IPv6 if it weren't still a joke in the US but here we are.
Yup, CGNAT sucks. But STUN works fine for me, and most games support it, so it's not a huge issue.
I could pay extra for a public IP, but for the same price I can get a VPS and do other cool stuff, so I just went the WireGuard VPN route. Same end result with a little more latency, but also more flexibility. I host a few static sites directly on the VPS, with everything else going through the VPN, so that's nice.
I'm not defending Proton. I don't even use them.
Edit: The region limits thing is nice though. It's not why I got the VPN, but it's nice to not have to pay to watch the Olympics and just watch it via the CBC or the BBC.