A smart VPN will avoid going to jail for you by not storing any of the data law enforcement wants in the first place.
Privacy
A place to discuss privacy and freedom in the digital world.
Privacy has become a very important issue in modern society, with companies and governments constantly abusing their power, more and more people are waking up to the importance of digital privacy.
In this community everyone is welcome to post links and discuss topics related to privacy.
Some Rules
- Posting a link to a website containing tracking isn't great, if contents of the website are behind a paywall maybe copy them into the post
- Don't promote proprietary software
- Try to keep things on topic
- If you have a question, please try searching for previous discussions, maybe it has already been answered
- Reposts are fine, but should have at least a couple of weeks in between so that the post can reach a new audience
- Be nice :)
Related communities
much thanks to @gary_host_laptop for the logo design :)
Yeah, Mullvad was searched and they shrugged and said "well, go ahead" and could then proudly publish that the Swedish authorities could take zero info from there: https://mullvad.net/en/blog/update-the-swedish-authorities-answered-our-protocol-request
Just recently signed up for Mullvad... No CC numbers or email addresses, you just get a string of numbers and that's all you need to connect with it anywhere. And you can pay with Monero.
It's like the paranoid person's dream.
Heck, if you want, you can pay with hard cash by mailing it with your payment token to their office. It's pretty great when it comes to choice of privacy.
Wondering how these magicians measure quality of service then, since they collect no juicy data. I find this hard to believe.
Quality of service is usually only useful with aggregate data which is worthless for prosecuting an individual.
In this blog post we explain why competent service operators can avoid having to share sensitive information about you without facing severe legal consequences. The reasons laid out will also highlight why you are better off choosing a VPN service run by privacy activists who will prioritise principles before profits in difficult situations
is it me or does it read like someone used an LLM to write those sentences?
Sounds like the intro paragraph to someone's term paper at uni.
This is usually how I intro documentation for tech projects. Its good practice for technical docs, doesn't necessarily mean its an LLM
Yeah, that's what I was going to say. Thank god that shit didn't exist when I was in college, or every paper I ever wrote would have been flagged. I guess I write like a robot.
Worth noting that there is a strong correlation between neurodivergence and falsely getting flagged for using AI. Apparently AI sounds autistic, so lots of autistic kids were getting flagged for AI use even when they wrote it themselves.
But if it helps, even ChatGPT has had to admit that AI detection is inaccurate and schools shouldn’t be relying on them.
the twist is that the LLM writes like this because you trained it to do so with your term papers that it scraped
Haha same! There's a place for us though: if you ever get into research, robotic writing tends to work out fairly well!
Thing is, I don't even feel like I do write like a robot per-se... Maybe it's more like I write like the average of every person who has ever written anything ever lol.
GPT loves alliteration, so at least there’s something to support your suspicion.
Verifiably no logs without court order (I'm guessing canary pages have gone the way of the dodo now, probably boilerplate in the orders, maybe wrong according to the article, perhaps in some jurisdictions) would be awesome. Verified by external audit is about as good as we can get, so proton, tutanota, I think, others muchly appreciated. I think one of them setup their OS in volatile RAM, which is cool, but probably not legally protective.
No, I don't expect you to go to jail for me, but due diligence minimising knowledge will bump you up my list of providers to choose.
One problem here is those that do verify, usually don't allow torrenting ports, so, no ratios for you. Anyone know what the over/under is on lesser tier VPNs that port share vs a VPS (with all its potential, but which country?) vs Usenet? Looking to have a clue when the time comes, knowledge gratefully accepted :)
I love Mullvad and recommend them for everything other than torrenting. Once they disabled port forwarding I moved to AirVPN who seem to be pretty legit.
I'm not trying to keep my ratios up but I have a few torrents of media that are not available anywhere for sale and have less than 10 seeds, so I feel like I am helping keep the shows and movies of my childhood alive.
They did have a server seized (physically) in 2015: https://lemmy.dbzer0.com/post/6754830
Though apparently there were no logs.
Interestingly though, that forum post was now deleted from AirVPN site. Strange...
Hmm, TIL, thanks.
Good person. Much like I would like to do. I'd be happy with a VPN for personal use and another one for torrenting (gluetun compatible preferably) Shall look at AirVPN, thanks.
Just switched to Mullvad and haven't tried torrenting with it yet... Doesn't work? Or just slow?
yes, but you can only download from peers with port forwarding enabled, and you can also only upload to port forwarding peers, so generally its fine for downloading, but if you want to keep ratio (uploading) on a private tracker you need port forwarding
I mean, if you set up your os on an encrypted ram disk, then set it to restart when the server rack door was unlocked/opened and didn't leave a backdoor for yourself to remote in, you could have a situation where you entirely lack the capability to give them access to anything before that moment. A skilled hacker might be able to get in through an exploit or do something crazy with cryogenics to read the memory at the time of shutdown, but a quick restart would overwrite most of what's in memory and scrub that
Legally, there's not much better defense than "I'm sorry your honor, I can't provide access to the running system in the same way I can't un-shatter a smashed mug". If someone shows up with a warrant, you could explain that it'll wipe itself if they open or unplug it, and it might've done so already. Then you guide them to it, hand over the key to the server cabinet, and let them decide to open the cabinet and destroy evidence so they can take it with them. Or they can take you at your word, and give up.
Court orders can't break physics, and as a VPN your reasoning for setting up the system like this is to make your service more appealing to customers - the purpose is not to aid in a crime or destroy evidence, it's just the normal course of business.
The same way that most companies wipe their emails after 30 days - yes, it potentially destroys incriminating paper trails, but that's just a side effect of the security policy you've had all along
Granted, there's probably some sketchy sealed laws they could use to force you to backdoor your own system moving forward, but you can fight that as it's undue hardship. It requires a non-negligible amount of work and would make your product less competitive
They might win in the end if they keep pushing, and even might be able to order you to "keep up the canary paper" (meaning keep claiming not even you have access to the running system), but more likely they'd get a warrant for your customer financial records and try to find an easier path to find what they want elsewhere
You really dont need to do all that if you just dont log to begin with
True, it's probably overkill. But even if you don't log, they could theoretically start live monitoring the VPN with a court order... With a setup like this, there's no front door or backdoor, just an ephemeral image you have to restart to modify. You'd have to write in access methods and rebuild to get in... The government can't just walk in and demand you stop what you're doing and build something for them
It does add security, even if you might not need that level of security
And here I thought companies can't go to jail. Apparently that only applies to the companies who aren't run by the lizard people or the kids popular with the priests.
The only reason I look at IVPN is because they allow port forwarding
They no longer offer this, right?
They don't?
Soooo how to split the packets up between 3 VPNs to make each providers piece useless?
You're about 15% of the way to re-inventing Tor.
check out Nym, they are doing this kind of network
Sounds very similar to Safing Privacy Network. They route different applications across nodes (Tor-esque).
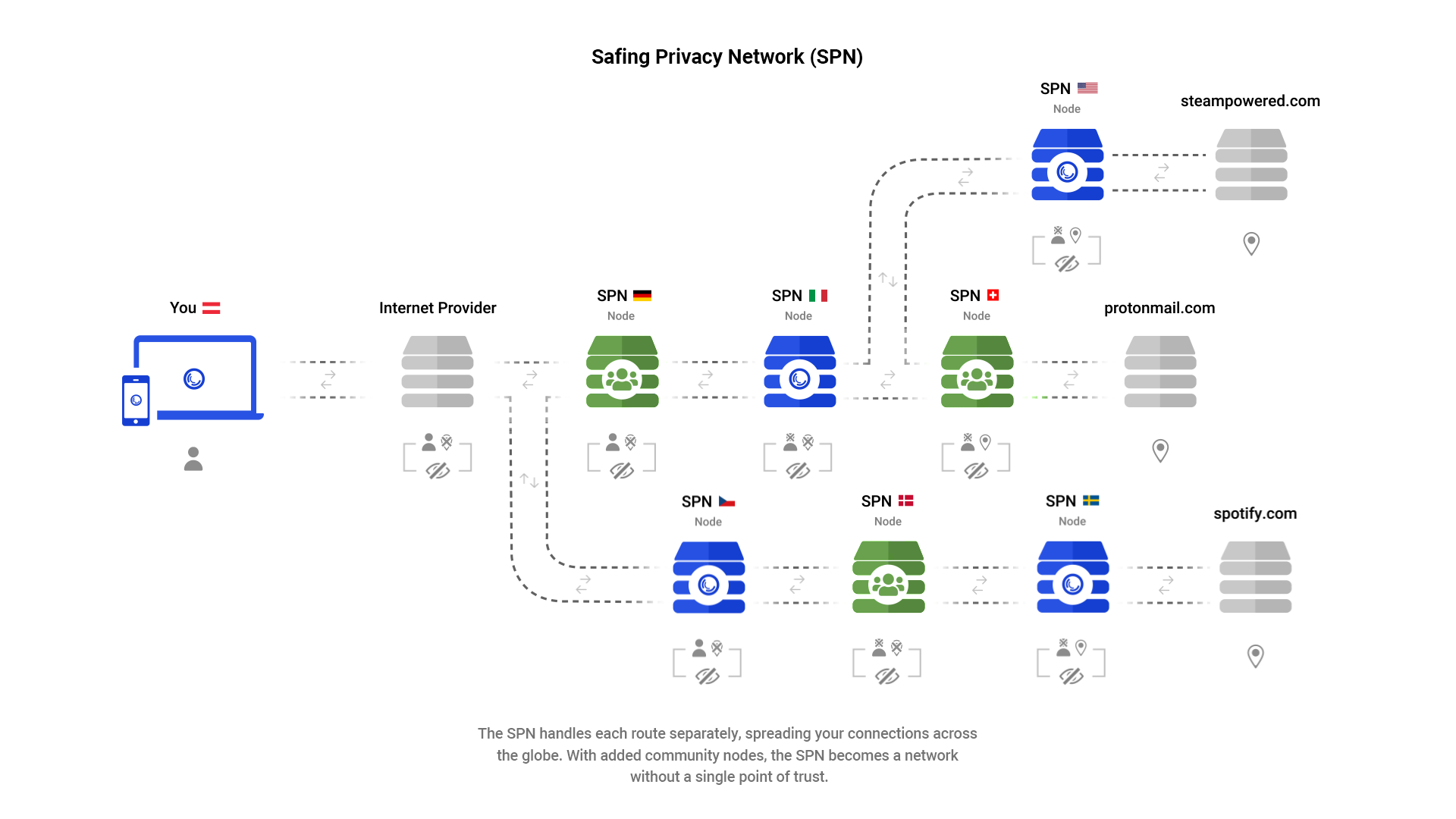
That does not work unless you involve yet another party after the VPNs and before the destination to rebuild the packets, as the destination won't know what to do with these split packets.
At that point you may be better off using an anonymity network with or without the VPN.
I’ve tried IVPN a number of times but it never works for getting around mlb.tv blackouts which is my biggest use case. ExpressVPN has just been reliable for me in that regard.