Can you link to that line in the code? I'm not seeing it, nor am I seeing the Internet permission being declared in AndroidManifest.xml
 Nigeria Launcher 😲
Nigeria Launcher 😲
Depending on which slicer you use, you can probably merge them as an assembly. I use Orca Slicer and after loading a model I can then right click on it and add an STL to it. Then it's a matter of positioning and lining them up. Once done you can slice it as one model.
It's GPLv3 so what's the pirate connection?
As an android enthusiast, who also is into the 3D printing scene, my first thought was "what does this launcher have to do with OctoPi and OctoPrint?".
The answer, nothing... obviously. Guess it's just an SEO and a me problem 🤪
I have a copy that was part of a humble bundle. It doesn't want to install on my phone, probably an issue with newer version of Android, but if you DM me I can share that with you if you want.
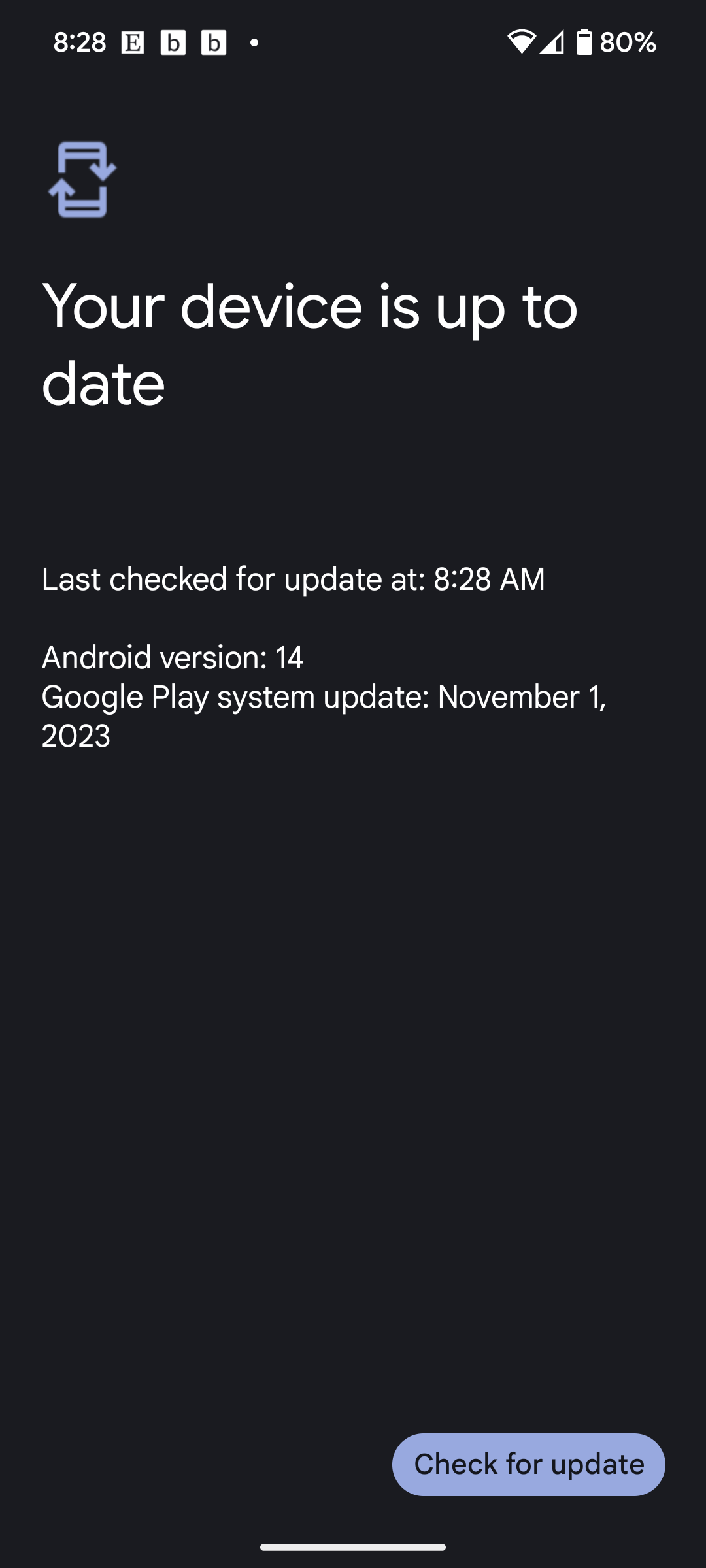 I just checked and it turns up to date on the November patch so they likely pulled it once shit started hitting the fan.
I just checked and it turns up to date on the November patch so they likely pulled it once shit started hitting the fan.
What about the fact that LAN only mode also allegedly still sends logs and data?
There's not much to mod if you have the first gen hardware. A 3D printed part and a paperclip can get the exploit going for ya
How do they work?
The carrier can look at the packets TTL and assume if it's not what they expect then it must have originated from another device via the hotspot. Verizon did, or maybe still does, use this to throttle hotspot traffic but not data originating from the phone.
Since I'm into 3D printing, I know of this project: https://github.com/gaifeng8864/klipper-on-android
It allows an android device to run a printer that uses the klipper firmware.