Windows Server OSes running CrowdStrike affected too
This VPN protocol usually uses a private key (client) / public key (server) combo that is used to connect through a public IP address (the 2 nodes can’t communicate it without) using the specified TCP or UDP (more often lately) and port to create the VPN tunnel that’s gets established during the handshakes.
There is a whole lot more going on with the process but that’s a high level view. But I have a WireGuard VPN service running on a raspberry pi that I put in a DMZ on my perimeter firewall.
But a port scanner would be able to see that port is open. Make sure you keep your software up to date. Hopefully the software devs of the VPN application is keeping their stuff up to date to avoid any vulnerabilities getting exposed in the code and a backdoor getting created because of it. As long as that doesn’t become an issue, no one will be able to get through without the private key. And those are usually uncrackable in a lifetime with the complexity and length of the key.
This is horrible. I run several different environments of VMware Instant Clone VDIs and use the SetUserFTA to help a users default browser and other file extension defaults to persist for a user from session to session on a non-persistent VDI. Now it’s broken.
Thanks a lot Microsoft. 😤
Talk less and listen more.
Realize that there is always someone that knows more than you do about any subject. Be humble knowing that you can always learn more.
Tempting to short the stock and say $&@# you Spez!
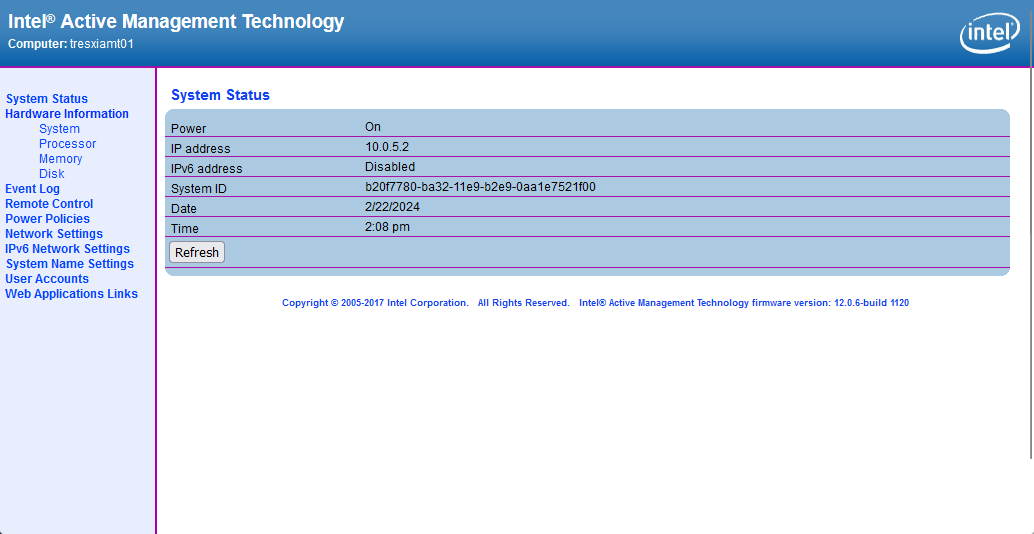
Ok, I grabbed a few screen shots for you as well. Here is a site that will link you to MEBx setup that enables AMT: http://h10032.www1.hp.com/ctg/Manual/c03883429
When power on your ProDesk G3, you can access the MEBx setup by pressing Ctrl+P or they also say F6 or Escape will get you there. Intel AMT runs on a different IP address than what your OS gets. You can assign DHCP or a static IP address and setup your admin password. You can then access the portal from http://ipaddress:16992 There should be a method of access what would show on the screen through a KVM like access but I use MeshCentral for that so I couldn't tell you how to do it without.
Hopefully, that gives you a start. Feel free to reach back out if you have any questions. Thank you!

2024 - Mexicans at the border (you know it’s already happening)
Lots of fluids and sleep. Remember the more she vomits, the more dehydrated she could get. So more water than normal.
For next time, if anyone takes too much go find some CBD. That will really help a person sober up in regards to THC.
There is a BSOD viewer by Nirsoft that is free located here: https://www.nirsoft.net/utils/blue_screen_view.html
This will allow you to take a look at the dump files that were created with each BSOD and typically give you the file name that typically is involved. Can you get that information and let us know what it gives you. This will give you a better idea of what the cause is.
I couldn’t see it the wrong way at all until I really stared at it. Then once I saw it, I couldn’t unsee it. lol
Unfortunately, the coding that the site uses to post your questions and return data back to you does not function in that matter. If you want to interact with the Large Language model without using you web browser, you would need to so by using other software or applications to hit their API (you do have to pay for this service) and then return the data back to you. So it is possible, but not in the manner that you are suggesting.
On a side note, I signed up for a 3 month trial of access to hit their API using a session code and a post shortcut on my iPhone. I created a iOS shortcut that allowed me to use OpenAI as a replacement for Siri. It was a fun little project.
No it has not. Validated on Ubuntu 16.04, 18.04, 20.04, 22.04 running CrowdStrike Sensor